How Does a Hash Help Secure Blockchain Technology?
1 Way Hashing Secures Blockchain – Blockchain technology is revolutionizing digital transactions, data storage, and cybersecurity. At the core of its security lies cryptographic hashing, a method that ensures integrity, immutability, and protection against fraud.

1. What is a Hash in Blockchain?
A hash is a fixed-length string generated from input data of any size using a cryptographic hash function. This function converts data into a unique representation, making it impossible to reverse-engineer the original input. In blockchain, hashing is used to secure transactions, link blocks, and validate information.
Key Features of a Hash:
- Fixed-Length Output: Regardless of input size, the hash output remains the same length.
- Unique Fingerprint: Even a minor change in input produces a drastically different hash.
- Irreversible: The original data cannot be retrieved from the hash.
- Deterministic: The same input always produces the same hash.
- Fast Computation: Hashing functions process data quickly.

Popular cryptographic hash functions used in blockchain include SHA-256 (Secure Hash Algorithm 256-bit), which Bitcoin and other cryptocurrencies rely on for security.
2. How Hashing Secures Blockchain Transactions
Every transaction in a blockchain is hashed before being added to a block. This ensures data integrity and security. Here’s how:
Transaction Verification
- When a user initiates a transaction, its details (sender, receiver, amount, timestamp) are converted into a hash.
- This hash acts as a unique digital fingerprint.
- The network nodes verify the hash before approving the transaction.
- Once verified, the transaction is permanently added to the blockchain.
Hashes ensure that transactions remain unchanged. If someone tries to alter a transaction, the hash changes, flagging the modification as invalid.
Preventing Double-Spending
Double-spending occurs when someone tries to use the same digital asset twice. Blockchain prevents this using hashing:
- Each transaction is hashed and stored in a block.
- A consensus mechanism (Proof-of-Work or Proof-of-Stake) validates transactions before adding them.
- Miners/validators ensure transactions are legitimate by checking hashes.
- If an altered transaction hash doesn’t match the stored hash, it is rejected.
1 Way Hashing Secures Blockchain
3. Hashing in Blockchain Blocks
Each block in a blockchain contains several components that use hashing for security:
- Block Hash: A unique identifier generated from the block’s contents.
- Merkle Root: A hash representing all transactions in the block.
- Previous Block Hash: A reference to the previous block’s hash, forming a chain.
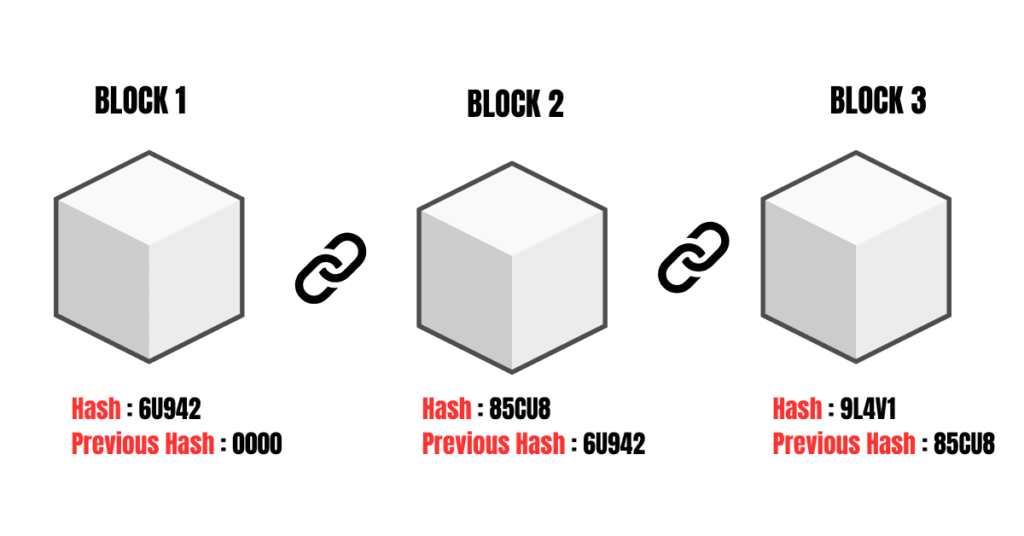
How Hashing Links Blocks Together
- A new block is created with a hash of all its transactions.
- The hash of the previous block is included in the new block.
- This linking creates an immutable chain.
- If an attacker tries to modify one block, all subsequent block hashes become invalid.
This chaining mechanism ensures that once data is recorded in a blockchain, it cannot be altered without re-mining all following blocks, which is computationally impossible in a large network.
4. Role of Hashing in Proof-of-Work (PoW) and Proof-of-Stake (PoS)
Blockchain security relies on consensus mechanisms to validate transactions. Hashing plays a crucial role in these processes.
Hashing in Proof-of-Work (PoW)
PoW, used in Bitcoin, requires miners to solve complex cryptographic puzzles to add new blocks. Here’s how:
- Miners compete to find a hash that meets certain criteria.
- They change a number called a nonce until they generate a valid hash.
- The first miner to find the correct hash gets to add the block and is rewarded.
- The solution is shared across the network, and nodes verify its validity.
Since changing a block would require solving the puzzle again for all subsequent blocks, PoW makes altering blockchain data infeasible.
Hashing in Proof-of-Stake (PoS)
In PoS-based blockchains like Ethereum 2.0, validators stake cryptocurrency to be chosen for block validation. Hashing ensures:
- Randomized selection of validators.
- Secure verification of transaction hashes.
- Prevention of fraudulent block creation.
5. How Hashing Prevents Tampering and Fraud
Immutability and Data Integrity
Once a transaction is recorded and hashed, it cannot be altered. If even a single character in a block is modified, the resulting hash changes completely, breaking the chain and making fraud detectable.
Resistance to Hacks
- Hash Collision Resistance: It is nearly impossible for two different inputs to produce the same hash, preventing fraudulent transactions.
- Distributed Storage: Since blockchain is decentralized, altering data requires modifying thousands of copies simultaneously, which is infeasible.
6. Additional Uses of Hashing in Blockchain
Smart Contracts Security
Smart contracts rely on hashing to verify the integrity of contract data. Any unauthorized changes to contract code result in a different hash, preventing fraud.
Digital Signatures and Authentication
Hashing helps secure digital signatures used in transactions. When signing a transaction, a user’s private key generates a unique hash, ensuring authenticity and preventing forgery.
Data Storage and File Integrity
Hashing allows blockchain networks to store large datasets efficiently. Platforms like IPFS (InterPlanetary File System) use hashing to track file changes and maintain data authenticity.
7. Real-World Examples of Blockchain Hashing
Bitcoin Transactions
Each Bitcoin transaction is hashed and stored in a Merkle Tree, ensuring data integrity and efficient verification.
Ethereum Smart Contracts
Ethereum uses hashing in its smart contracts to store contract states securely and prevent tampering.
Supply Chain Management
Companies like IBM and Walmart use blockchain hashing to track goods, ensuring authenticity and preventing counterfeiting.
Healthcare Records
Blockchain hashes protect patient records by ensuring data cannot be altered without detection, improving medical data security.
1 Way Hashing Secures Blockchain – FAQs
1. Why is hashing important in blockchain?
Hashing ensures data integrity, security, and immutability. It prevents fraud, secures transactions, and links blocks together in a chain.
2. Can a hash be reversed to get the original data?
No, cryptographic hash functions are designed to be one-way, making it impossible to derive the original input from a hash.
3. How does hashing prevent blockchain tampering?
If someone tries to alter a block’s data, the hash changes, invalidating all following blocks and alerting the network to tampering attempts.
4. What is SHA-256, and why is it used in blockchain?
SHA-256 is a cryptographic hash function that produces a 256-bit hash. It is widely used in blockchain due to its security, efficiency, and collision resistance.
5. How does hashing improve blockchain scalability?
Hashing enables efficient transaction verification through Merkle Trees, reducing the amount of data nodes need to process and store.
1 Way Hashing Secures Blockchain
Summary
Hashing is a fundamental security feature of blockchain technology. It ensures data integrity, prevents fraud, and maintains an immutable record of transactions. By securing blocks, verifying transactions, and supporting consensus mechanisms, hashing makes blockchain networks reliable and trustworthy.
Which Blockchain is Core Most Aligned With?

